Read more of this story at Slashdot.
Shared posts
Phone App That Watches Your Driving Habits Leads To Privacy Concerns
More Data on Attributing the Sony Attack
An analysis of the timestamps on some of the leaked documents shows that they were downloaded at USB 2.0 speeds -- which implies an insider.
Our Gotnews.com investigation into the data that has been released by the "hackers" shows that someone at Sony was copying 182GB at minimum the night of the 21st -- the very same day that Sony Pictures' head of corporate communications, Charles Sipkins, publicly resigned from a $600,000 job. This could be a coincidence but it seems unlikely. Sipkins's former client was NewsCorp and Sipkins was officially fired by Pascal's husband over a snub by the Hollywood Reporter.Two days later a malware bomb occurred.
We are left with several conclusions about the malware incident:
- The "hackers" did this leak physically at a Sony LAN workstation. Remember Sony's internal security is hard on the outside squishy in the center and so it wouldn't be difficult for an insider to harm Sony by downloading the material in much the same way Bradley Manning or Edward Snowden did at their respective posts.
- If the "hackers" already had copies, then it's possible they made a local copy the night of the 21st to prepare for publishing them as a link in the malware screens on the 24th.
Sony CEO Michael Lynton's released emails go up to November 21, 2014. Lynton got the "God'sApstls" email demand for money on the 21st at 12:44pm.
Other evidence implies insiders as well:
Working on the premise that it would take an insider with detailed knowledge of the Sony systems in order to gain access and navigate the breadth of the network to selectively exfiltrate the most sensitive of data, researchers from Norse Corporation are focusing on this group based in part on leaked human resources documents that included data on a series of layoffs at Sony that took place in the Spring of 2014.The researchers tracked the activities of the ex-employee on underground forums where individuals in the U.S., Europe and Asia may have communicated prior to the attack.
The investigators believe the disgruntled former employee or employees may have joined forces with pro-piracy hacktivists, who have long resented the Sony's anti-piracy stance, to infiltrate the company's networks.
I have been skeptical of the insider theory. It requires us to postulate the existence of a single person who has both insider knowledge and the requisite hacking skill. And since I don't believe that insider knowledge was required, it seemed unlikely that the hackers had it. But these results point in that direction.
Pointing in a completely different direction, a linguistic analysis of the grammatical errors in the hacker communications implies that they are Russian speakers:
Taia Global, Inc. has examined the written evidence left by the attackers in an attempt to scientifically determine nationality through Native Language Identification (NLI). We tested for Korean, Mandarin Chinese, Russian, and German using an analysis of L1 interference. Our preliminary results show that Sony's attackers were most likely Russian, possibly but not likely Korean and definitely not Mandarin Chinese or German.
The FBI still blames North Korea:
The FBI said Monday it was standing behind its assessment, adding that evidence doesn't support any other explanations."The FBI has concluded the government of North Korea is responsible for the theft and destruction of data on the network of Sony Pictures Entertainment. Attribution to North Korea is based on intelligence from the FBI, the U.S. intelligence community, DHS, foreign partners and the private sector," a spokeswoman said in a statement. "There is no credible information to indicate that any other individual is responsible for this cyber incident."
Although it is now thinking that the North Koreans hired outside hackers:
U.S. investigators believe that North Korea likely hired hackers from outside the country to help with last month's massive cyberattack against Sony Pictures, an official close to the investigation said on Monday.As North Korea lacks the capability to conduct some elements of the sophisticated campaign by itself, the official said, U.S. investigators are looking at the possibility that Pyongyang "contracted out" some of the cyber work.
This is nonsense. North Korea has had extensive offensive cyber capabilities for years. And it has extensive support from China.
Even so, lots of security experts don't believe that it's North Korea. Marc Rogers picks the FBI's evidence apart pretty well.
So in conclusion, there is NOTHING here that directly implicates the North Koreans. In fact, what we have is one single set of evidence that has been stretched out into 3 separate sections, each section being cited as evidence that the other section is clear proof of North Korean involvement. As soon as you discredit one of these pieces of evidence, the whole house of cards will come tumbling down.
But, as I wrote earlier this month:
Tellingly, the FBI's press release says that the bureau's conclusion is only based "in part" on these clues. This leaves open the possibility that the government has classified evidence that North Korea is behind the attack. The NSA has been trying to eavesdrop on North Korea's government communications since the Korean War, and it's reasonable to assume that its analysts are in pretty deep. The agency might have intelligence on the planning process for the hack. It might, say, have phone calls discussing the project, weekly PowerPoint status reports, or even Kim Jong Un's sign-off on the plan.On the other hand, maybe not. I could have written the same thing about Iraq's weapons of mass destruction program in the run-up to the 2003 invasion of that country, and we all know how wrong the government was about that.
I also wrote that bluffing about this is a smart strategy for the US government:
...from a diplomatic perspective, it's a smart strategy for the US to be overconfident in assigning blame for the cyberattacks. Beyond the politics of this particular attack, the long-term US interest is to discourage other nations from engaging in similar behavior. If the North Korean government continues denying its involvement, no matter what the truth is, and the real attackers have gone underground, then the US decision to claim omnipotent powers of attribution serves as a warning to others that they will get caught if they try something like this.
Of course, this strategy completely backfires if the attackers can be definitely shown to be not from North Korea. Stay tuned for more.
EDITED TO ADD (12/31): Lots of people in the comments are doubting the USB claim.
maymay: “Repeat Rape: How do they get away with it?”, Part 1 of...
MassaPorrada.

It turns out that if you ask the right questions in just the right way, some men will actually tell you that they're rapists. They'll just…admit it.

The key is, don't use the word rape. Just ask them what they've done.

Researchers asked 1,882 men: "Have you ever tried to have oral sex with someone by using (or threatening to use) physical force—twisting their arm, holding them down, etc.—if they did not cooperate?"

and: "Have you ever had sexual intercourse with someone, even though they didn't want to, because they were too intoxicated to resist your advances?"
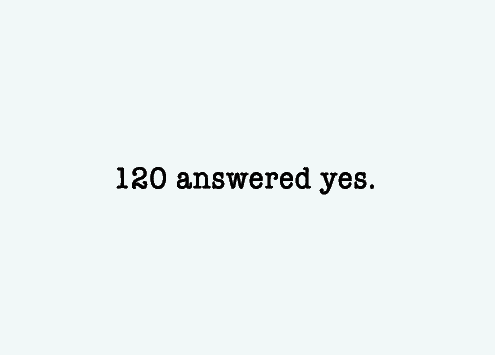
120 answered yes.

(That's rape.)

1,882 men…
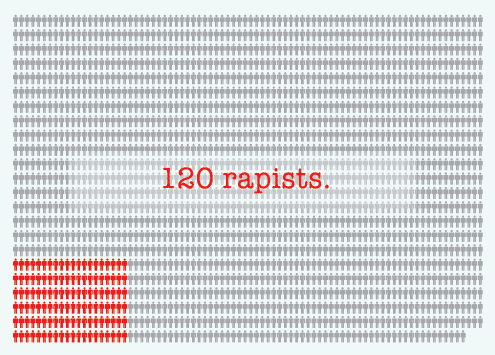
120 rapists.
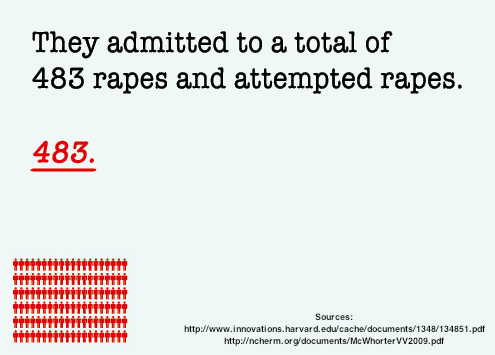
They admitted to a total of 483 rapes and attempted rapes. 483!

Whoa.
“Repeat Rape: How do they get away with it?”, Part 1 of 2. (link to Part 2)
Sources:
- College Men: Repeat Rape and Multiple Offending Among Undetected Rapists,Lisak and Miller, 2002 [PDF, 12 pages]
- Navy Men: Lisak and Miller’s results were essentially duplicated in an even larger study (2,925 men): Reports of Rape Reperpetration by Newly Enlisted Male Navy Personnel, McWhorter, 2009 [PDF, 16 pages]
By dark-side-of-the-room, who writes:
These infogifs are provided RIGHTS-FREE for noncommercial purposes. Repost them anywhere. In fact, repost them EVERYWHERE. No need to credit. Link to the L&M study if possible.
Knowledge is a seed; sow it.
We Can Avoid a Surveillance State Dystopia
MassaEu não concordo (que dá pra evitar a evasão de privacidade), mas queria a opinião dos amigos...
Read more of this story at Slashdot.
Computer Geeks As Loners? Data Says Otherwise
MassaSão sempre gregários e geralmente incultos, não sabem distinguir entre uma premissa maior e uma menor e têm escasso domínio do vernáculo.
Read more of this story at Slashdot.
Psychologists: Internet Trolls Are Narcissistic, Psychopathic, and Sadistic
MassaO instituto O RLY? de pesquisas psicológicas e psiquiátricas informa...
Read more of this story at Slashdot.
MAESTRO-II: NSA Exploit of the Day
MassaÓIA o tamanho do treco. Com um processador ARM7.
Today's item from the NSA's Tailored Access Operations (TAO) group implant catalog:
MAESTRO-II(TS//SI//REL) MAESTRO-II is a miniaturized digital core packaged in a Multi-Chip Module (MCM) to be used in implants with size constraining concealments.
(TS//SI//REL) MAESTRO-II uses the TAO standard implant architecture. The architecture provides a robust, reconfigurable, standard digital platform resulting in a dramatic performance improvement over the obsolete HC12 microcontroller based designs. A development Printed Circuit Board (PCB) using packaged parts has been developed and is available as the standard platform. The MAESTRO-II Multi-Chip-Module (MCM) contain an ARM7 microcontroller, FPGA, Flash and SDRAM memories.
Status: Available -- On The Shelf
Unit Cost: $3-4K
Page, with graphics, is here. General information about TAO and the catalog is here.
Finally -- I think this is obvious, but many people are confused -- I am not the one releasing these documents. Der Spiegel released these documents in December. Every national intelligence service, Internet organized crime syndicate, and clued terrorist organization has already pored over these pages. It's us who haven't really looked at, or talked about, these pages. That's the point of these daily posts.
In the comments, feel free to discuss how the exploit works, how we might detect it, how it has probably been improved since the catalog entry in 2008, and so on.
Sense the World with the Sensordrone [Deals Hub]
MassaSe alguém aqui do Old Reader me amar muito e achar que eu sou sempre um moleque bonzinho e mereço um presente de Natal, Aniversário, Dia das Crianças, ou semelhantes. Bônus= o trem tem um bafômetro embutido. :D
![Sense the World with the Sensordrone [Deals Hub]](http://cdn.iphonehacks.com/wp-content/themes/iph/timthumb.php?src=/wp-content/uploads/2014/01/Sensordrone.jpg&h=129&w=194&zc=1&q=100)
Peanut Allergy Treatment Trial In UK "A Success"
MassaAparentemente é o mesmo princípio das "vacinas para alergia" que eu tomava aos 12 anos de idade, subcutaneamente, por uns seis meses, todos os dias. Funciona muito...
Read more of this story at Slashdot.
GINSU: NSA Exploit of the Day
Massacompartilhado por que o nome é lindo.
Today's item from the NSA's Tailored Access Operations (TAO) group implant catalog:
GINSU(TS//SI//REL) GINSU provides software application persistence for the CNE implant, KONGUR, on target systems with the PCI bus hardware implant, BULLDOZER.
(TS//SI//REL) This technique supports any desktop PC system that contains at least one PCI connector (for BULLDOZER installation) and Microsoft Windows 9x, 2000, 20003, XP, or Vista.
(TS//SI//REL) Through interdiction, BULLDOZER is installed in the target system as a PCI bus hardware implant. After fielding, if KONGUR is removed from the system as a result of an operation system upgrade or reinstall, GINSU can be set to trigger on the next reboot of the system to restore the software implant.
Unit Cost: $0
Status: Released / Deployed. Ready for Immediate Delivery
Page, with graphics, is here. General information about TAO and the catalog is here.
In the comments, feel free to discuss how the exploit works, how we might detect it, how it has probably been improved since the catalog entry in 2008, and so on.
US Forces Coursera To Ban Students From Cuba, Iran, Sudan, and Syria
MassaPorque não existem proxies no mundo...
Read more of this story at Slashdot.
Bitcoin Exchange CEO Charlie Shrem Arrested On Money Laundering Charge
MassaIOW: bitcoin exchanges são proibidos no Zuza.
Read more of this story at Slashdot.
More Details About Mars Mystery Rock
Massaé um cocô
Read more of this story at Slashdot.
Meet COS, The Chinese Government's Contender To Battle iOS & Android
Massa1. sempre bom lembrar que na china, até a cauda longa é grossa :D
2. with blackjack and hookers!

The government of China is not too fond of foreign mobile operating systems like iOS and Android, so the country cooked up its own homegrown solution: A Linux-based, open-source operating system called the COS, or China Operating System.
According to People's Daily, a government-run news organization in China, COS is a joint effort between the Institute of Software at the Chinese Academy of Sciences (ISCAS) and a company called Shanghai Liantong, which develops software and communication technology. According to China’s dedicated website, the COS was designed for smartphones, PCs, smart appliances and set-top boxes, and is “intended to break the foreign monopoly in the field of infrastructure software.”
At a launch event Wednesday, the head of the ISCAS took the first steps in denigrating the so-called foreign mobile “monopoly” and promoting China’s own COS. According to Engadget Chinese, the ISCAS chief “criticized iOS for being a closed ecosystem,” mentioned Android’s “infamous fragmentation problem,” and added that both Android and Windows Phone OS are “let down by poor security.”
Many Chinese consumers are skeptical of COS in its early going. According to Quartz’ Jennifer Chiu, Chinese smartphone users took to Sina Weibo in droves to critique COS after its unveiling this week, poking fun at its name—“What does COS stand for? COPY ANOTHER SYSTEM?”—and sarcastically proposing that Communist Party “members, cadres, and leaders throw away their iPhones [first] and have them replayed by our superb homemade operating system!”
Justifiably Suspicious

Consumers have every right to be skeptical of its own government’s second attempt at a mobile operating system. That's right—second attempt.
China once tried to create its own Linux-based, open mobile ecosystem in the past, but the OPhone or OMS (Open Mobile System), fell flat after its 2009 release. The OPhone, though believed to be discontinued in 2010, is still alive today with a meager 600 available applications.
With COS, China is taking advantage of the recent NSA scandal in the U.S. to push its own product; and yet, a government-approved mobile operating system, especially in China of all places, reeks of its own backdoor exploits for governmental spying.
China, which has notably heavy restrictions against sociopolitical freedoms like access to the Internet, the right to assemble or practice religion, and even the right to bear children, has many times been accused of spying on (and censoring) its own citizens. More recently, Chinese officials have begun wiretapping each other’s bedrooms and showers out of distrust. Even China’s president was wiretapped by a member of the country’s own Communist Party.
See more: U.S. Fingers China For Cyber Espionage
Before it can go mainstream, COS will need to win support from a number of local carriers and handset makers, including ZTE, Lenovo and Huawei Technologies, the largest telecom equipment maker in the world, which was also accused of cyberspying in the U.S. and criticized for its ties to the Chinese military.
Lead image via Shutterstock; right images via China-COS
Irish Politician Calls For Crackdown On Open Source Internet Browsers
Massa'tava faltando gente falando "e tá pouco" pras trapalhadas da NSA."quem não deve não treme" e coisas assim...
Read more of this story at Slashdot.
Who Cares About 4K TVs?
Massa1080p downloads já são um saco.
If you believe the hype around the Consumer Electronics Show, 4K television is all the rage. TV makers have long hoped to spark demand for so-called ultra HD televisions, and this time around, they’re trying to ensure it by packaging the sets with some nifty new features.
The big question is whether anyone outside the consumer-electronics bubble here in Las Vegas will care. The answer: Probably not, at least until some of the newer software features migrate away from insanely priced hardware.
Judging by this morning’s sessions at CES, manufacturers like Sharp and Panasonic will be bringing their 4K TVs to market with a slew of new features such as better search and discovery, handy mobile apps, and in one case (via Panasonic’s VIERA Life+ Screen) even Kinect-like facial and voice recognition baked right in. Of course, that’s not all the 4K tech Panasonic has up its sleeve. The company also took the wraps off a new 4K wearable camera.
In unveiling its new AQUOS line—Aquos HD, Aquos 4K, Aquos Q, and the belle of its ball, the Aquos Q+—Sharp emphasized its Quattron Plus technology, which has 10 million more subpixels than full HD. But almost as a side note, the company took a moment to show off what's really cool—its "Smart Central" software. The interface takes a cue from streaming set-top boxes like Roku to make universal search and suggestions across all TV apps easier and more intuitive. And it comes with a companion remote control app that takes the drudgery out of entering search terms onscreen.
Such software is way more interesting than the hardware. The reason is obvious: These features may not be game-changing, but they're convenient and they stand a chance of coming to products that everyday people can actually afford sometime soon.
Not so for the hardware. Sharp did make a point of lowering the cost—within weeks, the 60- and 70-inch 4K Ultra HD series with 2160p resolution will go for $5,000 and $6,000 respectively, down from a 70-inch unit launched in September for $7,500. Can Samsung, LG and Sony do better? Not likely. This technology has been a wallet-gouger across the board, and that's even before you realize that there's very little to watch on these pricey new sets.
Until makers manage to shed those elitist prices, 4K televisions will remain little more than a matter of curiosity and hype, not essential entertainment gear.
To underscore the point, Sharp will also show off its 85-inch 8K television prototypes at CES again this year. Developed in conjunction with Dolby and Phillips, these innovations do push all sorts of envelopes. But as cool as glasses-free 3D on a mammoth, insanely high-resolution television is, it might as well be a holodeck. That would stand the same chance of landing in mainstream living rooms.
Images by Adriana Lee for ReadWrite
Headhunters Can't Tell Anything From Facebook Profiles
MassaFrom the O RLY Research Institute...
o primeiro comentário é ótimo:
<<
So a profession with no psychology background can't successfully evaluate peoples' personal statements and associations as a proxy for their professional competence? They're failing to do what even actual psychologists struggle with?
Wow. Who'd have seen that coming.
>>
Read more of this story at Slashdot.
Dogs Defecate In Alignment With Earth's Magnetic Field
Massanão sei o que comentar sobre isso.
Read more of this story at Slashdot.
The NSA Spies On America's Favorite Device—Time To Get Angry
Massa"time to get angry" foi quando o Snowden revelou a ponta do iceberg; a oportunidade já foi perdida IMHO.
If it seems these days like no gadget, website, service or function is safe from the data trolling of the U.S. National Security Administration, you are probably right. Even your iPhone is no barrier to the depths of the NSA’s capabilities, according to a new report.
Security researcher Jacob Applebaum gave a talk at the 30th Chaos Communication Congress in Hamburg, Germany yesterday outlining how the NSA has had the capability to break into an iPhone and siphon off of all the communications and activity on the device since 2008. German publication Der Spiegel also has its own extensive report showing that the NSA has a program called DROPOUTJEEP that is the codename of the iPhone hack.
In addition to the iPhone hack, the NSA has a unit called TAO—Tailored Access Operations—that has the primary duty of intercepting and bugging hardware (phones, laptops, servers) that various reports have stated HP and Cisco servers. Basically, the NSA can get at whatever it wants just about anywhere it wants. Der Spiegel also reports that the NSA has successfully tapped undersea fiber optics cables running from Europe, through the Middle East to Asia.
The iPhone hack stated by the documents in 2008 says that the NSA would need to have physical access to a device to be able to install its spyware. Once the spyware was in place, the NSA would have access to just about everything on the iPhone. The document said that a remote hack (one that doesn’t need physical access) was in the works for the future.
Applebaum from his talk at the 30th Chaos Communication Congress (via YouTube video):
SMS, contact list retrieval, voicemail, hot microphone, camera capture, cell tower location. You think Apple helped them with that? I don’t know. I hope Apple will clarify that. Here’s the problem. I don’t really believe that Apple didn’t help them. I can’t really prove it. They literally claim that any time they target an iOS device that it will succeed for implantation. Either they have a huge collection of exploits that will work against Apple products, meaning that they are hoarding information about critical systems that American companies produce and sabotaging them, or Apple sabotaged it themselves. Not sure which one it is. I’d like to believe that since Apple didn’t join the PRISM program until after Steve Jobs died, that maybe it’s just that they write shitty software. We know that’s true.Here is Applebaum's talk. The iPhone bit starts around 44:30:
Apple provided this response to technology publication a variety of technology publications this morning:
Apple has never worked with the NSA to create a backdoor in any of our products, including iPhone. Additionally, we have been unaware of this alleged NSA program targeting our products. We care deeply about our customers’ privacy and security. Our team is continuously working to make our products even more secure, and we make it easy for customers to keep their software up to date with the latest advancements. Whenever we hear about attempts to undermine Apple’s industry-leading security, we thoroughly investigate and take appropriate steps to protect our customers. We will continue to use our resources to stay ahead of malicious hackers and defend our customers from security attacks, regardless of who’s behind them.
Since the documents are from 2008, the extent of the NSA’s iPhone-snooping capability is not fully known. It may have had a working remote hack by this time. It may not and Apple may have closed the loop on this particular hardware bug that allowed the NSA in through the iPhones back door. The specifics actually do not matter quite as much because we have seen that the NSA, through one fashion or another, will get the information that it is looking for.
Time To Get Angry?
The Internet community, privacy experts, media and technology giants like Google, Facebook and Microsoft are all up in arms about NSA data mining and snooping. With each successive leak from the Edward Snowden files, every new report about the NSA’s clandestine activities (with each one seemingly more extreme than the last), the rhetoric raises and the saber rattling ensues.
The problem here is that the U.S. public doesn’t seem to care. The American public’s distrust of the government runs so deep that each successive NSA scandal is met with a collective shrug. The U.S. public has been watching crime scene investigation, police and spy dramas on television and film for so long that when they learn this activity is happening in real life, they give an apathetic nod. The constant news cycle where every tidbit of information is more dramatic than the last has desensitized the public to what is one of the biggest ongoing impactful stories of the century.
But they do love their iPhones.
The iPhone is consistently one of the most searched keywords on the Internet every year. People want to know when it is coming out, what new features it has, what bugs it needs to squash, how it compares to older iPhones and the top Android smartphones. Americans are enamored with Apple and the iPhone and have been since 2007.
Will the American public finally get say “I’m angry as hell and I’m not going to take it anymore!” when they learn that the U.S. government has had the ability to track everything on its most beloved gadget since almost the iPhone’s inception? Will this be the straw that finally spurs the public into an outraged shrill, demanding reform from the U.S. government to shape up the NSA once and for all?
The iPhone is the most personal of consumer devices. People seemingly have intimate relationships with their iPhones. Will learning that the NSA can violate that personal relationship and their privacy all at once might lead them to the outraged indignation that the Technorati have been craving? Maybe but probably not. People will continue to think, “Oh, that is stuff that happens to somebody else” and continue to watch their CSI shows, blissfully aware but purposefully ignorant that the foundations of their freedom are being put to the test.
NetfliXBMC Brings a Better, Remote-Controlled Netflix to XBMC
MassaThis is huge. (Netflix was a Silverlight-thing)

With a good home theater PC, you can play just about anything—though Netflix has always been a bit difficult. A new XBMC add-on called NetfliXBMC makes the process simpler and more streamlined than ever. Here's how to set it up.
There have been a few Netflix add-ons out there, but because Netflix uses Silverlight and some tight DRM, it's always been hard to integrate with XBMC. NetfliXBMC, created by user AddonScriptorDE is the best add-on we've seen yet, and it only takes a few minutes to set up.
What You'll Need
Unlike other XBMC add-ons, it's not as simple as installing the add-on and running it. You'll want to download a few things before you start:
- XBMC 12 "Frodo" running on Windows, OS X, or Linux. We're going to use Windows in this guide, but will note where those differences are. If you're using our $500 media center build or something similar, this guide should get you through the process very smoothly. Linux users will need to install Pipelight as described on the add-ons page.
- Chrome, Safari, or Internet Explorer. NetfliXBMC requires a browser to play videos, so you'll need one of these installed (Firefox is not currently supported). We're going to use Chrome in this guide.
- A Netflix account. For obvious reasons.
Step One: Install Chrome Launcher and NetfliXBMC

You'll need two add-ons to get this working, and you won't find them in the default XBMC repository. So, to install them:
- Download AddonScriptorDE's testing repository here. Save it to your Downloads folder (or wherever else you want).
- Open XBMC and head to Settings > Add-Ons > Install from ZIP file. Choose the ZIP file you just downloaded and it should install the repository.
- Head to Get Add-Ons and choose AddonScriptorDE's Testing Repo. If there isn't anything in it, head back to the Get Add-Ons Menu, press the "c" key to bring up the context menu, and choose "Force Refresh." If you head back to AddonScriptorDE's Testing Repo, you should see a list of categories.
- Head to Program Add-Ons and select "Chrome Launcher." Press Enter and install the add-on.
- Once Chrome Launcher is installed, head back to the category list and go to Video Add-Ons. Choose NetfliXBMC and install it.
Now, you should have all the necessary add-ons installed and you can continue to the next step.
Step Two: Configure NetfliXBMC

Next, you'll need to set up NetfliXBMC to work with your Netflix account and other preferences. Head to Videos > Video Add-Ons in XBMC, highlight NetfliXBMC, and press the "c" key to bring up the context menu. Choose "Add-On Settings" to get started. Here are some things you may want to tweak:
- Account > Email and Password: Enter your Netflix credentials here.
- Account > Single-User Account: If you have multiple profiles on your Netflix account, you'll want to de-select this (otherwise your browser will ask you every time, which isn't easily controllable with the remote). If you have multiple users using Netflix on the same XBMC machine, select the "Show Profile Selection on Each Start" option, which will ask you which user is watching every time you use the add-on.
- Advanced > Delete Cache/Delete Cookies: Try these buttons if you experience problems logging in.
- Advanced > Win Browser/OS X Browser: If you're using Internet Explorer or Safari instead of Chrome, you'll want to select your browser here.
Once you've gotten this set up, head into NetfliXBMC and try playing a movie or TV episode. If you experience problems, try fiddling with the settings to get it working, or check out the troubleshooting section at the bottom of this post.
If you can get a video to play, it's time for the last step: setting up your remote.
Step Three: Configure Your Remote (Optional)

If you control your home theater PC with a remote (rather than a mouse and keyboard), you'll need to configure NetfliXBMC for your remote as well.
On Windows, NetfliXBMC has a little helper app that runs in the background and maps the keys you specify to Netflix's built-in shortcuts. Head back to NetfliXBMC's settings, go to the Advanced tab, and head to Configure Control Utility. From there, just enter the keys you want to use for each task. You may have to look up which keys are mapped to which buttons on your remote to do this—though XBMC's default keyboard shortcuts are a good place to start.
We haven't tested the Mac and Linux versions, so check out NetfliXBMC's forum post for more info on controlling Netflix with your remote. Usually it just involves installing a small app separately and mapping your keys, just like the Windows instructions above.
If You Have Issues
NetfliXBMC is still very much in the early stages, but in our tests, it worked quite well. However, depending on your setup, you may or may not experience issues. Make sure you've read this entire guide word-for-word, as well as the NetfliXBMC forum post. If you still have questions, that thread is the best place to ask them, especially if it's the result of a bug that the developer needs to fix. He's extremely responsive, so don't be afraid to let him know if you're having trouble! Good luck!
TIL The view that men suppress female sexuality is contradicted by some findings. Evidence shows that women have worked to stifle each other's sexuality because sex is a limited resource that women use to negotiate with men, and scarcity gives women an advantage."
MassaPutz, eu concordo. Sempre achei que o tal deficit erótico era uma contrapartida à dominância física masculina. Será que alguma de nossas amigas não faria o favor de comentar/brigar/etc?
Bitcoin Explanation
MassaPara consulta :D
This is the best explanation of the Bitcoin protocol that I have read.
3 Questions to Ask at Dinner to Make Your Family Stronger
Massa"If your family reunion is not awkward enough, there are somethings you can try!"
If all else fails, you can climb on the table and start unzipping, asking "attention,... does anyone know which STD is this??"

More and more research studies are concluding that regular dinners are the key to a happy, healthy family. Dinnertime is a great time to discuss how well your family is working. The Week highlights an agile approach to this (something we've seen similarly applied to parenting in general).
Taking excerpts from the book The Secrets of Happy Families, The Week quotes Scrum software developer Jeff Sutherland's approach:
The centerpiece of the program is a weekly review session built on the principle of "inspect and adapt."
Three questions get asked:
1. What things went well in our family this week?
2. What things could we improve in our family?
3. What things will you commit to working on this week?
You don't have to actually fire off those questions directly like that, but those three things are good ones to discuss with your family on a regular basis. Just having regular dinners and meaningful conversations during them could improve just about everything parents worry about. If the agile approach isn't for you, try the 10-50-1 formula also taken from the book:
10. Aim for ten minutes of quality talk per meal. .. 50. Let your kids speak at least half the time. … 1. Teach your kids one new word every meal.
Hit up the link below for lots more family bonding advice.
The secrets of happy families | The Week
Photo by Lars Plougmann.
Dois poemas de uma polonesa
Massaporque poesia é importante, porra.
Hoje tive o prazer de ler dois poemas da polonesa Wisława Szymborska, publicados no excelente blog do escritor Carlos Emerson Junior (recomendadíssimo, aí na listinha da direita). Por 12 pequenas coletâneas de poemas, ela já abocanhou um Prêmio Nobel de Literatura, em 1996. Por aí se vê a força de seus textos.
Reproduzo abaixo os dois selecionados por Carlos, para que sempre possamos lê-los também por aqui ![]()
***
Cem pessoas
Em cada cem pessoas
Aquelas que sempre sabem mais:
cinquenta e duas.
Inseguras de cada passo:
quase todo o resto.
Prontas a ajudar,
desde que não demore muito:
quarenta e nove.
Sempre boas,
porque não podem ser de outra maneira:
quatro — bem, talvez cinco.
Capazes de admirar sem invejar:
dezoito.
Levadas ao erro
pela juventude (que passa):
sessenta, mais ou menos.
Aquelas com quem é bom não se meter:
quarenta e quatro.
Vivem com medo constante
de alguma coisa ou alguém:
setenta e sete.
Capazes de felicidade:
vinte e alguns, no máximo.
Inofensivos sozinhos,
selvagens em multidões:
mais da metade, por certo.
Cruéis,
quando forçados pelas circunstâncias:
é melhor não saber
nem aproximadamente.
Peritos em prever:
não muitos mais
que os peritos em adivinhar.
Tiram da vida nada além de coisas:
trinta
(mas eu gostaria de estar errada).
Dobradas de dor,
sem uma lanterna na escuridão:
oitenta e três,
mais cedo ou mais tarde.
Aqueles que são justos:
uns trinta e cinco.
Mas se for difícil de entender:
três.
Dignos de simpatia:
noventa e nove.
Mortais:
cem em cem –
um número que não tem variado.
***
Exemplo
O vendaval
à noite arrancou todas as folhas de uma árvore,
menos uma,
deixada
para balançar só num galho nu.
Com este exemplo
a Violência demonstra
que sim –
às vezes ela gosta de se divertir.
Arquivo em:Poemas Tagged: Carlos Emerson Junior, Cem Pessoas, Exemplo, Poemas, Poesia, Polônia, polonesa, Prêmio Nobel de Literatura, Wisława Szymborska
Sports in a nutshell. [vectorbelly]
MassaEspecialmente a última frase.
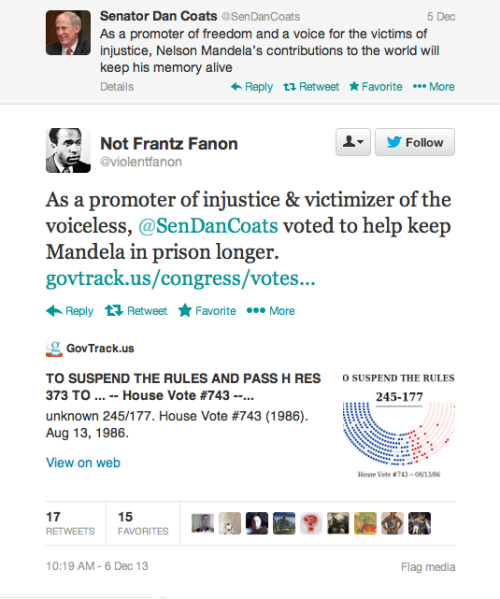
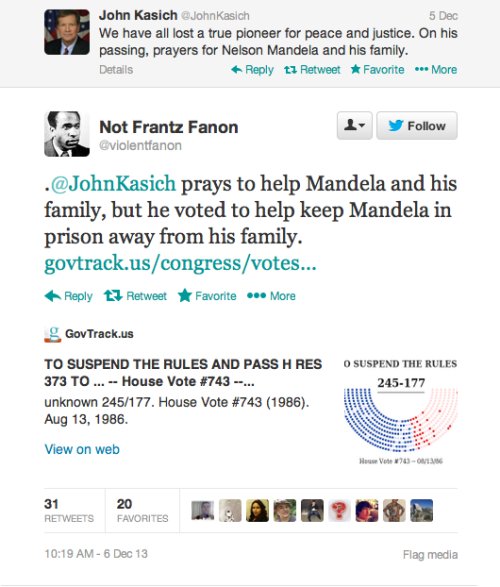
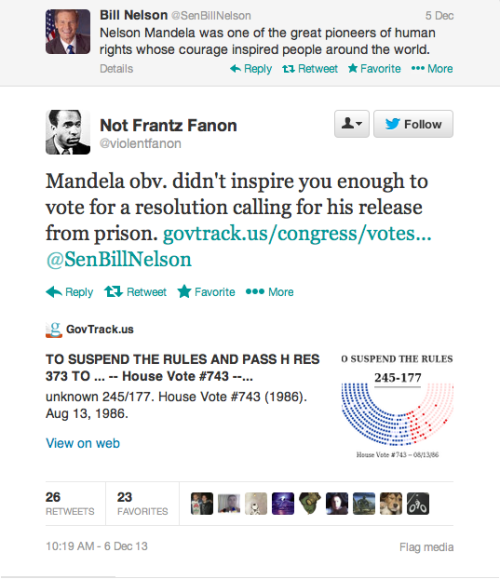
dolphin-spit: oswaldofguadalupe: The Twitter Mandela Hall Of...
MassaToma idiota, que as internetes não perdoam.
Aí a gente faz 4 anos de faculdade pra isso: Trabalhar por 500...
MassaEmpresa: teknisa informática. Informando pra todo mundo passar longe.

Aí a gente faz 4 anos de faculdade pra isso: Trabalhar por 500 pilas por mês. E se reclamar, é mal agradecido. As empresas costumam tratar funcionário/candidato como se estivessem fazendo um favor a eles, como se não precisassem deles. E aí surgem vagas com salários ridículos como o acima e/ou com condições de trabalho degradantes. Essa mentalidade escravocrata do empresariado brasileiro está fazendo com que muita mão de obra qualificada deixe o país. E isso só tente a piorar, IMHO.
Flatten the Web With This One-Click Bookmarklet

If you like a flatter design everywhere, websites with 3D buttons and other layout elements can be annoying. This neat little bookmarklet by developer Adam Schwartz promises to flatten any web page.
Basically, the bookmarklet removes background images. "Websites need to define a good background color behind their images, if they don't, you might see some unexpected things," Schwartz warns. And this has some unintended side effects, such as removing Twitter background images and making the YouTube subscribe button disappear. So try it out and see which websites it works on for you. It might make some less cluttered.
Head to the link below to get the bookmarklet and drag it to your bookmarks bar. Whenever you are on a website with 3D elements that feel like they're getting in the way, click it and it will automatically flatten the page.
Flatten the Web With This Bookmarklet | Hubspot