
Bewarethewumpus
Shared posts
“Snowden Treaty” Calls for End to Mass Surveillance, Protections for Whistleblowers
Inspired by the disclosures of NSA whistleblower Edward Snowden, a campaign for a new global treaty against government mass surveillance was launched today in New York City.
Entitled the “The International Treaty on the Right to Privacy, Protection Against Improper Surveillance and Protection of Whistleblowers,” or, colloquially, the “Snowden Treaty,” an executive summary of the forthcoming treaty calls on signatories “to enact concrete changes to outlaw mass surveillance,” increase efforts to provide “oversight of state surveillance,” and “develop international protections for whistleblowers.”
At the event launching the treaty, Snowden spoke via a video link to say that the treaty was “the beginning of work that will continue for many years,” aimed at building popular pressure to convince governments to recognize privacy as a fundamental human right, and to provide internationally-guaranteed protections to whistleblowers who come forward to expose government corruption. Snowden also cited the threat of pervasive surveillance in the United States, stating that “the same tactics that the NSA and the CIA collaborated on in places like Yemen are migrating home to be used in the United States against common criminals and people who pose no threat to national security.”
The treaty is the brainchild of David Miranda, who was detained by British authorities at Heathrow airport in 2013, an experience that he described as galvanizing him towards greater political activism on this issue. Miranda is the partner of Glenn Greenwald, a founding editor of The Intercept who received NSA documents from Snowden. Authorities at Heathrow seized files and storage devices that Miranda was transporting for Greenwald. (The Press Freedom Litigation Fund of First Look Media, the publisher of the Intercept, is supporting Miranda’s lawsuit challenging his detention.)
Along with the activist organization Avaaz, Miranda began working on the treaty project last year. “We sat down with legal, privacy and technology experts from around the world and are working to create a document that will demand the right to privacy for people around the world,” Miranda said. Citing ongoing efforts by private corporations to protect themselves from spying and espionage, Miranda added that “we see changes happening, corporations are taking steps to protect themselves, and we need to take steps to protect ourselves too.”
The full text of the treaty has yet to be released, but it is envisioned as being the first international treaty that recognizes privacy as an inalienable human right, and creates legally-mandated international protections for individuals who are facing legal persecution for exposing corruption in their home countries. Its proponents hope to build momentum and convince both governments and multi-national organizations to adopt its tenets. Since the Snowden revelations there has been increasing public recognition of the threat to global privacy, with the United Nations announcing the appointment of its first Special Rapporteur on this issue in March, followed by calls for the creation of a new Geneva Convention on internet privacy.
Greenwald also spoke at the event, saying, “This campaign offers the opportunity to put pressure on governments to adopt a treaty that pushes back against mass surveillance, and also makes clear that individuals who expose corruption should not be subject to the retribution of political leaders.” Adding that many governments that make a show of supporting the dissidents of other countries tend to persecute their own whistleblowers, Greenwald added, “We need a lot of public pressure to say that mass surveillance should end, and that people who expose corruption should be entitled to international protections.”
The post “Snowden Treaty” Calls for End to Mass Surveillance, Protections for Whistleblowers appeared first on The Intercept.
From Radio to Porn, British Spies Track Web Users’ Online Identities
THERE WAS A SIMPLE AIM at the heart of the top-secret program: Record the website browsing habits of “every visible user on the Internet.”
Before long, billions of digital records about ordinary people’s online activities were being stored every day. Among them were details cataloging visits to porn, social media and news websites, search engines, chat forums, and blogs.
The mass surveillance operation — code-named KARMA POLICE — was launched by British spies about seven years ago without any public debate or scrutiny. It was just one part of a giant global Internet spying apparatus built by the United Kingdom’s electronic eavesdropping agency, Government Communications Headquarters, or GCHQ.
The revelations about the scope of the British agency’s surveillance are contained in documents obtained by The Intercept from National Security Agency whistleblower Edward Snowden. Previous reports based on the leaked files have exposed how GCHQ taps into Internet cables to monitor communications on a vast scale, but many details about what happens to the data after it has been vacuumed up have remained unclear.
Amid a renewed push from the U.K. government for more surveillance powers, more than two dozen documents being disclosed today by The Intercept reveal for the first time several major strands of GCHQ’s existing electronic eavesdropping capabilities.
One system builds profiles showing people’s web browsing histories. Another analyzes instant messenger communications, emails, Skype calls, text messages, cell phone locations, and social media interactions. Separate programs were built to keep tabs on “suspicious” Google searches and usage of Google Maps.
The surveillance is underpinned by an opaque legal regime that has authorized GCHQ to sift through huge archives of metadata about the private phone calls, emails and Internet browsing logs of Brits, Americans, and any other citizens — all without a court order or judicial warrant.
Metadata reveals information about a communication — such as the sender and recipient of an email, or the phone numbers someone called and at what time — but not the written content of the message or the audio of the call.
As of 2012, GCHQ was storing about 50 billion metadata records about online communications and Web browsing activity every day, with plans in place to boost capacity to 100 billion daily by the end of that year. The agency, under cover of secrecy, was working to create what it said would soon be the biggest government surveillance system anywhere in the world.
Radio radicalization
The power of KARMA POLICE was illustrated in 2009, when GCHQ launched a top-secret operation to collect intelligence about people using the Internet to listen to radio shows.
The agency used a sample of nearly 7 million metadata records, gathered over a period of three months, to observe the listening habits of more than 200,000 people across 185 countries, including the U.S., the U.K., Ireland, Canada, Mexico, Spain, the Netherlands, France, and Germany.
A summary report detailing the operation shows that one aim of the project was to research “potential misuse” of Internet radio stations to spread radical Islamic ideas.
GCHQ spies from a unit known as the Network Analysis Center compiled a list of the most popular stations that they had identified, most of which had no association with Islam, like France-based Hotmix Radio, which plays pop, rock, funk and hip-hop music.
They zeroed in on any stations found broadcasting recitations from the Quran, such as a popular Iraqi radio station and a station playing sermons from a prominent Egyptian imam named Sheikh Muhammad Jebril. They then used KARMA POLICE to find out more about these stations’ listeners, identifying them as users on Skype, Yahoo, and Facebook.
The summary report says the spies selected one Egypt-based listener for “profiling” and investigated which other websites he had been visiting. Surveillance records revealed the listener had viewed the porn site Redtube, as well as Facebook, Yahoo, YouTube, Google’s blogging platform Blogspot, the photo-sharing site Flickr, a website about Islam, and an Arab advertising site.
GCHQ’s documents indicate that the plans for KARMA POLICE were drawn up between 2007 and 2008. The system was designed to provide the agency with “either (a) a web browsing profile for every visible user on the Internet, or (b) a user profile for every visible website on the Internet.”
The origin of the surveillance system’s name is not discussed in the documents. But KARMA POLICE is also the name of a popular song released in 1997 by the Grammy Award-winning British band Radiohead, suggesting the spies may have been fans.
A verse repeated throughout the hit song includes the lyric, “This is what you’ll get, when you mess with us.”
The Black Hole
GCHQ vacuums up the website browsing histories using “probes” that tap into the international fiber-optic cables that transport Internet traffic across the world.
A huge volume of the Internet data GCHQ collects flows directly into a massive repository named Black Hole, which is at the core of the agency’s online spying operations, storing raw logs of intercepted material before it has been subject to analysis.
Black Hole contains data collected by GCHQ as part of bulk “unselected” surveillance, meaning it is not focused on particular “selected” targets and instead includes troves of data indiscriminately swept up about ordinary people’s online activities. Between August 2007 and March 2009, GCHQ documents say that Black Hole was used to store more than 1.1 trillion “events” — a term the agency uses to refer to metadata records — with about 10 billion new entries added every day.
As of March 2009, the largest slice of data Black Hole held — 41 percent — was about people’s Internet browsing histories. The rest included a combination of email and instant messenger records, details about search engine queries, information about social media activity, logs related to hacking operations, and data on people’s use of tools to browse the Internet anonymously.
Throughout this period, as smartphone sales started to boom, the frequency of people’s Internet use was steadily increasing. In tandem, British spies were working frantically to bolster their spying capabilities, with plans afoot to expand the size of Black Hole and other repositories to handle an avalanche of new data.
By 2010, according to the documents, GCHQ was logging 30 billion metadata records per day. By 2012, collection had increased to 50 billion per day, and work was underway to double capacity to 100 billion. The agency was developing “unprecedented” techniques to perform what it called “population-scale” data mining, monitoring all communications across entire countries in an effort to detect patterns or behaviors deemed suspicious. It was creating what it said would be, by 2013, “the world’s biggest” surveillance engine “to run cyber operations and to access better, more valued data for customers to make a real world difference.”
GCHQ is able to identify a particular person’s website browsing habits by pulling out the raw data stored in repositories like Black Hole and then analyzing it with a variety of systems that complement each other.
KARMA POLICE, for instance, works by showing the IP addresses of people visiting websites. IP addresses are unique identifiers that are allocated to computers when they connect to the Internet.
In isolation, IPs would not be of much value to GCHQ, because they are just a series of numbers — like 195.92.47.101 — and are not attached to a name. But when paired with other data they become a rich source of personal information.
To find out the identity of a person or persons behind an IP address, GCHQ analysts can enter the series of numbers into a separate system named MUTANT BROTH, which is used to sift through data contained in the Black Hole repository about vast amounts of tiny intercepted files known as cookies.
Cookies are automatically placed on computers to identify and sometimes track people browsing the Internet, often for advertising purposes. When you visit or log into a website, a cookie is usually stored on your computer so that the site recognizes you. It can contain your username or email address, your IP address, and even details about your login password and the kind of Internet browser you are using — like Google Chrome or Mozilla Firefox.
For GCHQ, this information is incredibly valuable. The agency refers to cookies internally as “target detection identifiers” or “presence events” because of how they help it monitor people’s Internet use and uncover online identities.
If the agency wants to track down a person’s IP address, it can enter the person’s email address or username into MUTANT BROTH to attempt to find it, scanning through the cookies that come up linking those identifiers to an IP address. Likewise, if the agency already has the IP address and wants to track down the person behind it, it can use MUTANT BROTH to find email addresses, usernames, and even passwords associated with the IP.
Once the agency has corroborated a targeted person’s IP address with an email address or username, it can then use the tiny cookie files associated with these identifiers to perform a so-called “pattern of life” analysis showing the times of day and locations at which the person is most active online.
the agency was extracting data containing information about people’s visits to the adult website YouPorn
In turn, the usernames and email and IP addresses can be entered into other systems that enable the agency to spy on the target’s emails, instant messenger conversations, and web browsing history. All GCHQ needs is a single identifier — a “selector,” in agency jargon — to follow a digital trail that can reveal a vast amount about a person’s online activities.
A top-secret GCHQ document from March 2009 reveals the agency has targeted a range of popular websites as part of an effort to covertly collect cookies on a massive scale. It shows a sample search in which the agency was extracting data from cookies containing information about people’s visits to the adult website YouPorn, search engines Yahoo and Google, and the Reuters news website.
Other websites listed as “sources” of cookies in the 2009 document (see below) are Hotmail, YouTube, Facebook, Reddit, WordPress, Amazon, and sites operated by the broadcasters CNN, BBC, and the U.K.’s Channel 4.
In one six-month period between December 2007 and June 2008, the document says, more than 18 billion records from cookies and other similar identifiers were accessible through MUTANT BROTH.
The data is searched by GCHQ analysts in a hunt for behavior online that could be connected to terrorism or other criminal activity. But it has also served a broader and more controversial purpose — helping the agency hack into European companies’ computer networks.
In the lead up to its secret mission targeting Netherlands-based Gemalto, the largest SIM card manufacturer in the world, GCHQ used MUTANT BROTH in an effort to identify the company’s employees so it could hack into their computers.
The system helped the agency analyze intercepted Facebook cookies it believed were associated with Gemalto staff located at offices in France and Poland. GCHQ later successfully infiltrated Gemalto’s internal networks, stealing encryption keys produced by the company that protect the privacy of cell phone communications.
Similarly, MUTANT BROTH proved integral to GCHQ’s hack of Belgian telecommunications provider Belgacom. The agency entered IP addresses associated with Belgacom into MUTANT BROTH to uncover information about the company’s employees. Cookies associated with the IPs revealed the Google, Yahoo, and LinkedIn accounts of three Belgacom engineers, whose computers were then targeted by the agency and infected with malware.
The hacking operation resulted in GCHQ gaining deep access into the most sensitive parts of Belgacom’s internal systems, granting British spies the ability to intercept communications passing through the company’s networks.
Cryptome surveillance
In March, a U.K. parliamentary committee published the findings of an 18-month review of GCHQ’s operations and called for an overhaul of the laws that regulate the spying. The committee raised concerns about the agency gathering what it described as “bulk personal datasets” being held about “a wide range of people.” However, it censored the section of the report describing what these “datasets” contained, despite acknowledging that they “may be highly intrusive.”
The Snowden documents shine light on some of the core GCHQ bulk data-gathering programs that the committee was likely referring to — pulling back the veil of secrecy that has shielded some of the agency’s most controversial surveillance operations from public scrutiny.
KARMA POLICE and MUTANT BROTH are among the key bulk collection systems. But they do not operate in isolation — and the scope of GCHQ’s spying extends far beyond them.
The agency operates a bewildering array of other eavesdropping systems, each serving its own specific purpose and designated a unique code name, such as: SOCIAL ANTHROPOID, which is used to analyze metadata on emails, instant messenger chats, social media connections and conversations, plus “telephony” metadata about phone calls, cell phone locations, text and multimedia messages; MEMORY HOLE, which logs queries entered into search engines and associates each search with an IP address; MARBLED GECKO, which sifts through details about searches people have entered into Google Maps and Google Earth; and INFINITE MONKEYS, which analyzes data about the usage of online bulletin boards and forums.
GCHQ has other programs that it uses to analyze the content of intercepted communications, such as the full written body of emails and the audio of phone calls. One of the most important content collection capabilities is TEMPORA, which mines vast amounts of emails, instant messages, voice calls and other communications and makes them accessible through a Google-style search tool named XKEYSCORE.
As of September 2012, TEMPORA was collecting “more than 40 billion pieces of content a day” and it was being used to spy on people across Europe, the Middle East, and North Africa, according to a top-secret memo outlining the scope of the program. The existence of TEMPORA was first revealed by The Guardian in June 2013.
To analyze all of the communications it intercepts and to build a profile of the individuals it is monitoring, GCHQ uses a variety of different tools that can pull together all of the relevant information and make it accessible through a single interface.
SAMUEL PEPYS is one such tool, built by the British spies to analyze both the content and metadata of emails, browsing sessions, and instant messages as they are being intercepted in real time.
One screenshot of SAMUEL PEPYS in action shows the agency using it to monitor an individual in Sweden who visited a page about GCHQ on the U.S.-based anti-secrecy website Cryptome.
Domestic spying
Partly due to the U.K.’s geographic location — situated between the United States and the western edge of continental Europe — a large amount of the world’s Internet traffic passes through its territory across international data cables.
In 2010, GCHQ noted that what amounted to “25 percent of all Internet traffic” was transiting the U.K. through some 1,600 different cables. The agency said that it could “survey the majority of the 1,600” and “select the most valuable to switch into our processing systems.”
Many of the cables flow deep under the Atlantic Ocean from the U.S. East Coast, landing on the white-sand beaches of Cornwall in the southwest of England. Others transport data between the U.K. and countries including France, Belgium, Germany, the Netherlands, Denmark, and Norway by crossing below the North Sea and coming aground at various locations on England’s east coast.
According to Joss Wright, a research fellow at the University of Oxford’s Internet Institute, tapping into the cables allows GCHQ to monitor a large portion of foreign communications. But the cables also transport masses of wholly domestic British emails and online chats, because when anyone in the U.K. sends an email or visits a website, their computer will routinely send and receive data from servers that are located overseas.
“I could send a message from my computer here [in England] to my wife’s computer in the next room and on its way it could go through the U.S., France, and other countries,” Wright says. “That’s just the way the Internet is designed.”
In other words, Wright adds, that means “a lot” of British data and communications transit across international cables daily, and are liable to be swept into GCHQ’s databases.
GCHQ is authorized to conduct dragnet surveillance of the international data cables through so-called external warrants that are signed off by a government minister.
The external warrants permit the agency to monitor communications in foreign countries as well as British citizens’ international calls and emails — for example, a call from Islamabad to London. They prohibit GCHQ from reading or listening to the content of “internal” U.K. to U.K. emails and phone calls, which are supposed to be filtered out from GCHQ’s systems if they are inadvertently intercepted unless additional authorization is granted to scrutinize them.
However, the same rules do not apply to metadata. A little-known loophole in the law allows GCHQ to use external warrants to collect and analyze bulk metadata about the emails, phone calls, and Internet browsing activities of British people, citizens of closely allied countries, and others, regardless of whether the data is derived from domestic U.K. to U.K. communications and browsing sessions or otherwise.
In March, the existence of this loophole was quietly acknowledged by the U.K. parliamentary committee’s surveillance review, which stated in a section of its report that “special protection and additional safeguards” did not apply to metadata swept up using external warrants and that domestic British metadata could therefore be lawfully “returned as a result of searches” conducted by GCHQ.
Perhaps unsurprisingly, GCHQ appears to have readily exploited this obscure legal technicality. Secret policy guidance papers issued to the agency’s analysts instruct them that they can sift through huge troves of indiscriminately collected metadata records to spy on anyone regardless of their nationality. The guidance makes clear that there is no exemption or extra privacy protection for British people or citizens from countries that are members of the Five Eyes, a surveillance alliance that the U.K. is part of alongside the U.S., Canada, Australia, and New Zealand.
“If you are searching a purely Events only database such as MUTANT BROTH, the issue of location does not occur,” states one internal GCHQ policy document, which is marked with a “last modified” date of July 2012. The document adds that analysts are free to search the databases for British metadata “without further authorization” by inputing a U.K. “selector,” meaning a unique identifier such as a person’s email or IP address, username, or phone number.
Authorization is “not needed for individuals in the U.K.,” another GCHQ document explains, because metadata has been judged “less intrusive than communications content.” All the spies are required to do to mine the metadata troves is write a short “justification” or “reason” for each search they conduct and then click a button on their computer screen.
Intelligence GCHQ collects on British persons of interest is shared with domestic security agency MI5, which usually takes the lead on spying operations within the U.K. MI5 conducts its own extensive domestic surveillance as part of a program called DIGINT (digital intelligence).
“We think and behave differently based on the assumption that people may be watching.”
GCHQ’s documents suggest that it typically retains metadata for periods of between 30 days to six months. It stores the content of communications for a shorter period of time, varying between three to 30 days. The retention periods can be extended if deemed necessary for “cyber defense.”
One secret policy paper dated from January 2010 lists the wide range of information the agency classes as metadata — including location data that could be used to track your movements, your email, instant messenger, and social networking “buddy lists,” logs showing who you have communicated with by phone or email, the passwords you use to access “communications services” (such as an email account), and information about websites you have viewed.
Records showing the full website addresses you have visited — for instance, www.gchq.gov.uk/what_we_do — are treated as content. But the first part of an address you have visited — for instance, www.gchq.gov.uk — is treated as metadata.
In isolation, a single metadata record of a phone call, email, or website visit may not reveal much about a person’s private life, according to Ethan Zuckerman, director of Massachusetts Institute of Technology’s Center for Civic Media.
But if accumulated and analyzed over a period of weeks or months, these details would be “extremely personal,” he told The Intercept, because they could reveal a person’s movements, habits, religious beliefs, political views, relationships, and even sexual preferences.
For Zuckerman, who has studied the social and political ramifications of surveillance, the most concerning aspect of large-scale government data collection is that it can be “corrosive towards democracy” — leading to a chilling effect on freedom of expression and communication.
“Once we know there’s a reasonable chance that we are being watched in one fashion or another it’s hard for that not to have a ‘panopticon effect,’” he said, “where we think and behave differently based on the assumption that people may be watching and paying attention to what we are doing.”
Light oversight
A GCHQ spokesman declined to answer any specific questions for this story, citing a “longstanding policy” not to comment on intelligence matters. The spokesman insisted in an emailed statement that GCHQ’s work is “carried out in accordance with a strict legal and policy framework, which ensures that our activities are authorised, necessary and proportionate, and that there is rigorous oversight.”
It is unclear, however, whether there are sufficient internal checks in place in practice to ensure GCHQ’s spies don’t abuse their access to the troves of personal information.
According to agency’s documents, just 10 percent of its “targeting” of individuals for surveillance is audited annually and a random selection of metadata searches are audited every six months.
When compared to surveillance rules in place in the U.S., GCHQ notes in one document that the U.K. has “a light oversight regime.”
The more lax British spying regulations are reflected in secret internal rules that highlight greater restrictions on how NSA databases can be accessed. The NSA’s troves can be searched for data on British citizens, one document states, but they cannot be mined for information about Americans or other citizens from countries in the Five Eyes alliance.
No such constraints are placed on GCHQ’s own databases, which can be sifted for records on the phone calls, emails, and Internet usage of Brits, Americans, and citizens from any other country.
The scope of GCHQ’s surveillance powers explain in part why Snowden told The Guardian in June 2013 that U.K. surveillance is “worse than the U.S.” In an interview with Der Spiegel in July 2013, Snowden added that British Internet cables were “radioactive” and joked: “Even the Queen’s selfies to the pool boy get logged.”
In recent years, the biggest barrier to GCHQ’s mass collection of data does not appear to have come in the form of legal or policy restrictions. Rather, it is the increased use of encryption technology that protects the privacy of communications that has posed the biggest potential hindrance to the agency’s activities.
“The spread of encryption … threatens our ability to do effective target discovery/development,” says a top-secret report co-authored by an official from the British agency and an NSA employee in 2011.
“Pertinent metadata events will be locked within the encrypted channels and difficult, if not impossible, to prise out,” the report says, adding that the agencies were working on a plan that would “(hopefully) allow our Internet Exploitation strategy to prevail.”
———
Documents published with this article:
- TDI Introduction
- TINT External July 2009
- Social Anthropoid Briefing
- Sensitive Targeting Authorisation
- QFD BLACKHOLE Technology Behind INOC
- Pull Steering Group Minutes
- Access: Vision 2013
- Op Highland Fling Event Log
- Operational Engineering November 2010
- NGE BLACK HOLE ConOp
- Next Generation Events
- Events Analysis
- Legalities
- JCE UK Legalities Context
- HRA Auditing
- GCHQ Analytic Cloud Challenges
- Events
- Demystifying NGE Rock Ridge
- Data Stored in BLACK HOLE
- Cyber Defence Operations Legal Policy
- Crypt Discovery Activity
- Content-Metadata Matrix
- Cloud Developers Exchange July 2011
- Broadcast Analysis
- Blazing Saddles Tools
- Architecture Risk 2012
- ADD SD BLACK HOLE
- 200G Iris Access
The post From Radio to Porn, British Spies Track Web Users’ Online Identities appeared first on The Intercept.
Kenan & Kel Reunite for "Good Burger" Sketch
Actors Kenan Thompson and Kel Mitchell reunited on The Tonight Show Starring Jimmy Fallon to perform a sketch based on their 1997 comedy film Good Burger.
No sign of safety risks with longterm pot use for chronic pain

(credit: Thomas Hawk @ Flickr)
While the medical use of cannabis has expanded, there's little data available regarding its safety. Although the drug has been used (recreationally and medically) by humans going back far into prehistory, it was criminalized by the time researchers began conducting rigorous clinical trials. Consequently, almost every news story one reads about the use of cannabis as a medical therapy contains some variation of disclaimer saying "more research is needed" into the longterm safety of medical cannabis use.
Now a tiny bit of that "more research" has been published in the Journal of Pain. The headline result was that there was no increase in the number of serious adverse events in a group that used cannabis for chronic pain when compared to a group that did not. As the authors point out in the paper, the "lack of data on the safety and efficacy of cannabis is a major barrier to physicians’ involvement [in prescribing medical cannabis]."
The study was conducted in Canada between 2004 and 2008. It followed 431 chronic pain patients for a year in order to assess the rates of adverse events, pulmonary effects, and neurocognitive function. The patients were divided into a group that used cannabis to treat that chronic pain (n=215) as well a control group that didn't (n=216). A key strength of the work is that it was a prospective study; the participants were chosen before they started the treatment plan.
Man arrested for disparaging police on Facebook settles suit for $35,000

(credit: mkhmarketing)
A Wisconsin man arrested for posting disparaging and profanity laced comments on a local police department's Facebook page has settled a civil rights lawsuit and is being awarded $35,000.
Thomas G. Smith used the Facebook page of a rural Wisconsin village called Arena to, among other things, label local cops as "fucking racists bastards."
He was charged criminally in state court on allegations of disorderly conduct and unlawful use of computerized communications. He was sentenced to a year of probation and 25 hours of community service. A state appeals court overturned his conviction last year.
Songwriter says he made $5,679 from 178 million Spotify streams

The songwriter who co-wrote Meghan Trainor's "All About That Bass" alleged on Tuesday that he only cleared $5,679 from more than 178 million streams of the song on Spotify. (credit: YouTube)
A Tuesday copyright roundtable discussion, hosted by Nashville's Belmont University and led by the House Judiciary Committee, opened with one of the past year's most successful songwriters announcing just how little money he'd made from more than 178 million streams of a song he co-wrote: $5,679.
That means Nashville songwriter Kevin Kadine, the co-writer of the hit 2014 Meghan Trainor song "All About That Bass," made close to $31.90 for every million streams. According to a report by The Tennessean, Kadine didn't clarify to the roundtable's five members of the House of Representatives exactly how the songwriting proceeds were split between himself and Trainor (who shared songwriting credits on "Bass"), but he did allege that the average streaming-service payout for a song's songwriting team is roughly $90 per million streams.
"That's as big a song as a songwriter can have in their career, and number one in 78 countries," Kadine said. "But you're making $5,600. How do you feed your family?"
Ousted Volkswagen CEO Might Still Get $67M Payday, Plus Company Car
The Wall Street Journal reports that Martin Winterkorn, who stepped down from his gig atop the German automaker yesterday, already had about $33 million in his VW pension at the end of 2014. And according to the company’s annual report, there’s a severance payout rule that pays up to two years worth of their total annual remuneration.
That could mean another $34 million for Winterkorn, that is if the VW board says so. There is also the promise of a company car. We have some suggestions for some “clean diesel” models he should consider.
See, the only way Winterkorn — or any VW exec at the top level — can get that two-year severance deal is if it’s determined he left the job through no fault of his own. But as the Journal points out, the annual report doesn’t spell out exactly how the board determines issues of fault in these matters.
Of course, $67 million is a dust particle compared to the $18 billion smog cloud that VW could have to inhale if the Environmental Protection Agency chooses to pursue the maximum penalty for each car VW sold in the U.S. with software designed to cheat on emissions tests.
And then there are the growing number of class action suits being filed, state-level investigations, and possible criminal prosecution by the U.S. Justice Department.
The One Thing Pope Francis Could Say That Would Truly Stun Congress
There are many things Pope Francis could say in his Thursday address to Congress that would make its members uncomfortable. Rep. Paul Gosar, a Republican Catholic from Arizona, has already announced that he’s refusing to attend because the Pope may urge action on global warming. The Pope could also strongly criticize capitalism, as he did in great detail in his 2013 apostolic exhortation The Joy of the Gospel.
But the Pope’s critique of the world has an even more radical component, one that’s gotten little notice in the United States — maybe because it’s so radical that many Americans, members of Congress in particular, might not even understand what he’s saying.
And what Francis is saying is that capitalism and our growing environmental disasters are rooted in an even older, larger problem: centuries of European colonialism. Moreover, he suggests this colonialism has never really ended, but merely changed forms — and much of U.S. foreign policy that’s purportedly about terrorism, or drugs, or corruption, or “free trade,” is actually colonialism in disguise.
That’s a perspective that no one in Congress — from Ted Cruz to Bernie Sanders or anyone in between — is going to get behind.
The Pope’s most extensive denunciation of colonialism is probably his speech last June at the World Meeting of Popular Movements (an event nurtured by the Vatican at the Pope’s initiative) in Santa Cruz, Bolivia. It’s genuinely startling. Read this and try to imagine what would happen if it were spoken at the U.S. Capitol:
The Earth, entire peoples and individual persons are being brutally punished. And behind all this pain, death and destruction there is the stench of what Basil of Caesarea called “the dung of the devil.” … Once capital becomes an idol and guides people’s decisions, once greed for money presides over the entire socioeconomic system, it ruins society, it condemns and enslaves men and women. …
Let us always have at heart the Virgin Mary, a humble girl from small people lost on the fringes of a great empire. … Mary is a sign of hope for peoples suffering the birth pangs of justice. …
We see the rise of new forms of colonialism, which seriously prejudice the possibility of peace and justice. … The new colonialism takes on different faces. At times it appears as the anonymous influence of mammon: corporations, loan agencies, certain “free trade” treaties, and the imposition of measures of “austerity,” which always tighten the belt of workers and the poor. … At other times, under the noble guise of battling corruption, the narcotics trade and terrorism — grave evils of our time, which call for coordinated international action — we see states being saddled with measures which have little to do with the resolution of these problems and which not infrequently worsen matters.
Moreover, the location of the event and the Pope’s speech was certainly not random. Bolivia today is an international symbol of both the evils of European colonialism and resistance to it, with history running from the founding of La Paz in 1548 to right now.
For instance, while it’s almost completely unknown in Europe and the U.S., an estimated 8 million indigenous Bolivians and enslaved Africans died mining silver for Spain from the Bolivian mountain Cerro Rico — or as it’s known in Bolivia, “The Mountain That Eats Men.” Potosí, the city that grew up around Cerro Rico, is now extraordinarily polluted, and the mountain is still being mined, often by children. On the conquerors’ side of the ledger, Potosí was the source of tens of thousands of tons of silver, leading to the Spanish phrase vale un potosi — i.e., worth a fortune. (Some also believe the U.S. dollar sign originated from the design of coins minted there.)
More recently, in a faint echo of Potosí, the International Monetary Fund tried to force the Bolivian city of Cochabamba to lease its water system to a consortium of international investors. Enormous, successful protests helped make then-Congressman Evo Morales famous — enough so that he went on to become Bolivia’s first-ever indigenous president.
Morales kicked out the U.S. Drug Enforcement Agency in 2008, and now the U.S. has secretly indicted several Bolivian officials connected to his administration — under, as the Pope might put it, “the noble guise of battling the narcotics trade.” The U.S. also appears to have been behind the forcing down of Morales’ presidential plane as it flew across Europe from Moscow, because the U.S. believed Morales might have had Edward Snowden onboard.
This history is why the Pope could tell Bolivians, “I do not need to go on describing the evil effects of this subtle dictatorship: you are well aware of them.”
And whether white people are ready to hear it or not, Bolivia’s experience is the norm across the planet, not the exception. It’s why President Cristina Fernández de Kirchner of Argentina said what happened to Morales’ plane was “the vestiges of a colonialism that we thought was completely overcome.” Or why most of the world sees the Israel-Palestine conflict as not about democracy vs. terrorism, but about colonialism. Or why it sees the Trans-Pacific Partership as not about free trade vs. protectionism, but about colonialism. Or why it saw the invasion of Iraq as not about weapons of mass destruction, but colonialism.
Based on the current presidential race, I’d estimate that the U.S. political system will have the maturity and grace to hear this in maybe 300 years. And if the Pope brings any of this up at the Capitol, it’s safe to say he’s not going to be invited back.
The post The One Thing Pope Francis Could Say That Would Truly Stun Congress appeared first on The Intercept.
China Pressures U.S. Companies to Buckle on Strong Encryption and Surveillance
Before Chinese President Xi Jinping visits President Obama, he and Chinese executives have some business in Seattle: pressing U.S. tech companies, hungry for the Chinese market, to comply with the country’s new stringent and suppressive Internet policies.
The New York Times reported last week that Chinese authorities sent a letter to some U.S. tech firms seeking a promise they would not harm China’s national security.
That might require such things as forcing users to register with their real names, storing Chinese citizens’ data locally where the government can access it, and building government “back doors” into encrypted communication products for better surveillance. China’s new national security law calls for systems that are “secure and controllable,” which industry groups told the Times in July means companies will have to hand over encryption keys or even source code to their products.
Among the big names joining Xi at Wednesday’s U.S.-China Internet Industry Forum: Apple, Google, Facebook, IBM and Microsoft.
The meeting comes as U.S. law enforcement officials have been pressuring companies to give them a way to access encrypted communications. The technology community has responded by pointing out that any sort of hole for law enforcement weakens the entire system to attack from outside bad actors — such as China, which has been tied to many instances of state-sponsored hacking into U.S systems.
In fact, one argument privacy advocates have repeatedly made is that back doors for law enforcement would set a dangerous precedent when countries like China want the same kind of access to pursue their own domestic political goals.
But here, potentially, the situation has been reversed, with China using its massive economic leverage to demand that sort of access right now.
Human rights groups are urging U.S. companies not to give in.
“U.S. tech firms need to put people and principles before profit, and defend Internet freedom,” William Nee, a China researcher at Amnesty International, was quoted as saying in a statement Amnesty issued Tuesday night. “They must not turn a blind eye to China’s online repression in order to gain access to the lucrative Chinese market.”
Amnesty noted China’s already poor digital rights record, which includes the jailing of Chinese activists for voicing their opinions. Ilham Tohti, an academic who founded the website Uighur Online and criticized China’s treatment of the Muslim Uighur minority, was imprisoned exactly one year before Wednesday’s meeting for “separatism,” a charge Amnesty describes as “baseless.”
“Governments across the globe are increasingly using technology to crack down on freedom of expression, censor information on human rights violations and carry out indiscriminate mass surveillance in the name of security, often in collaboration with corporations,” the group wrote. “Internet companies have a responsibility to respect international human rights in their global operations. This entails putting proactive measures in place so that serious human rights abuses can be avoided.”
Marietje Schaake, a Dutch member of the European parliament who has written about the issue, told The Intercept that European and U.S. companies should reject “mandatory back doors or weakening of encryption standards.”
“In the short term it may seem tempting to enter the Chinese market on the government’s terms,” she wrote in an email, “but in the long run being a search engine that censors, or a social network that surveils, will scare away users.”
Adam Segal, a senior fellow focusing on China for the Council on Foreign Relations, said the companies “are likely to not sign any pledge voluntarily.”
When it comes to building back doors for the Chinese government, he told The Intercept, “They are going to hold off as long as possible. … Apple can’t give a speech and talk about its commitment to privacy and then give in to China. They can’t put up with the backlash that would hit them.”
When and if the Chinese are able to convince the companies to build weaker encryption, however, Segal said he thinks U.S. law enforcement will leap on that opportunity to get the same thing.
The post China Pressures U.S. Companies to Buckle on Strong Encryption and Surveillance appeared first on The Intercept.
New Lawsuit Claims Monkey Should Get Copyright & Royalties For Famous Selfie
This is according to animal rights organization PETA, who aren’t just making a theoretical claim that a monkey deserves equal treatment under copyright law, but who have gone so far as to file a lawsuit [PDF] in federal court.
A brief refresher: In 2011, photographer David Slater was taking photos of macaque monkeys in Indonesia when one of them grabbed a camera and snapped several photos, including the one shown above.
The image became popular online and was eventually added to the Wikimedia Commons collection of 22 million images and videos that are free to use.
Slater made repeated attempts, with varying success, to have the photo pulled, claiming he was the rightful copyright holder. But in Aug. 2014, the Wikimedia Foundation explained that its understanding of U.S. copyright law is that the copyright belongs to the photographer, not the camera owner. And since the photographer in this case was a monkey, who can’t legally hold copyright, the image is in the public domain.
A U.S. Copyright Office document released weeks later bolstered this argument, citing other examples where non-humans could be said to have made art but could still not hold copyright, like a mural painted by an elephant.
But PETA claims that the monkey, who is apparently named Naruto, should be treated as if he were a human artist who had taken the same photo.
“The Monkey Selfies resulted from a series of purposeful and voluntary actions by Naruto, unaided by Slater,” reads the complaint, “resulting in original works of authorship not by Slater, but by Naruto.”
Even though the Copyright Office made its stance clear on the issue of non-humans, the lawsuit contends that the actual law isn’t as unforgiving toward monkeys and other non-human artists, arguing that the Copyright Act itself is “sufficiently broad so as to permit the protections of the law to extend to any original work, including those created by Naruto.”
PETA contends that monkeys are similar to humans in many ways and are just as interested in visual stimuli as we are.
“Naruto and all crested macaques are highly intelligent, capable of advanced reasoning and learning from experience,” reads the complaint. “Like other primates, including humans, Naruto and all crested macaques have stereoscopic color vision with depth perception and are vision dominant. As a result, visual images, including seeing their reflection in a motor bike mirror or camera lens, are intensely interesting experiences for them.”
The complaint doesn’t simply argue that Naruto should be granted copyright, but that Slater is violating the monkey photographer’s copyright by making money from the sale of a book that uses Naruto’s photo.
Even if the U.S. Copyright Office says a non-human can not register a copyright, Naruto’s legal eagles try to make the case that their client took the images in Indonesia, and thus no copyright registration in the U.S. is needed.
At the same time they allege that Slater’s continued use of the photo is a violation of Naruto’s copyright under U.S. law.
PETA is seeking to have Naruto declared the copyright holder, for the court to enjoin Slater and others from using the photos taken by Naruto, for Naruto to receive appropriate payment for the use of his photos in Slater’s book, and for unspecified damages.
While Slater has not given up his battle to be considered the copyright holder for the monkey selfit, PETA uses Slater’s own words against him in the complaint.
According to the suit, the photographer wrote in his book, “The recognition that animals have personality and should be granted rights to dignity and property would be a great thing.”
DHS infosec chief: We should pull clearance of feds who fail phish test
In the wake of the Office of Personnel Management hack this year, which reportedly took advantage of a phishing attack to steal credentials used to gain access to highly sensitive personnel records, US federal agencies have been increasing their security training and employee testing around phishing. In addition to the employee awareness campaign launched by the National Counterintelligence and Security Center, more agencies are using security auditing tools that simulate phishing attacks against employees to test whether the employees abide by their information security training. Those who fall for phishing tests are generally either required to take a security refresher class or at worst are publicly called out for their errors in agency e-mails.
But at least one federal chief information security officer thinks that these steps aren't enough and that repeatedly falling for phishing attempts—fake or real—should have more dire consequences than a slap on the wrist. According to a report from DefenseOne, Department of Homeland Security CISO Paul Beckman said during a panel discussion at a cybersecurity event in Washington last week that he believes it's time to ban those who flunk Phishing 101 from having access to sensitive government data by revoking their clearances.
"Someone who fails every single phishing campaign in the world should not be holding a TS SCI [top secret, sensitive compartmentalized information—the highest level of security clearance] with the federal government," stated Beckman. "You have clearly demonstrated that you are not responsible enough to responsibly handle that information."
Leaks show that Microsoft writes release notes, so why can’t it publish them?
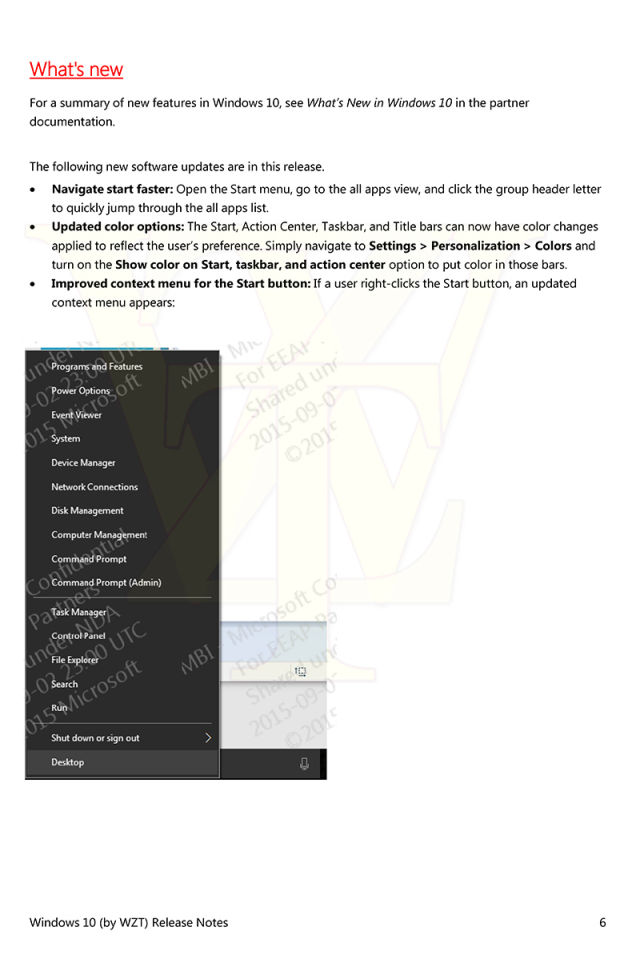
Over its short lifetime, Windows 10 has already received a number of cumulative updates that combine security fixes with some number of non-security bug fixes and perhaps even the occasional new feature. To be honest, we're not entirely sure what the cumulative updates contain, and there's a simple reason for that: while security updates do receive official documentation and enumeration, the non-security stuff is not described by Microsoft at all. When asked about this last month, Microsoft affirmed that it has no plans to tell anyone what's in the updates.
This is frustrating. If an organization is holding back on deploying Windows 10 because of bugs it has experienced, it would be useful to know if those bugs have been addressed. Even when Windows 10 has been deployed, it's helpful to know if a given build is supposed to fix a particular bug, as it can aid diagnosis of issues and make clear what's supposed to be happening, even if something isn't working correctly. Any user-visible functional changes make this even more important; if the operating system is going to change, people should be given some idea of what to expect.
At a time that Microsoft should be striving to build confidence in "Windows as a service" and its new update and release model, its peculiar reluctance to explain what goes into each update seems more likely to drive IT departments into using the infrequently updated Long Term Servicing Branch instead of the mainline Windows release. Microsoft's guidance is that LTSB should be used only on those mission critical systems that absolutely cannot tolerate anything more than security fixes, but if the company is going to keep people in the dark about what they're installing with each update, plumping for LTSB may well be the rational choice for the concerned administrator.
Government Argues: If Your Mobile Phone Provider Knows Where You Are, Why Shouldn’t We?
In one of the stronger defenses of Fourth Amendment rights in the digital age, a federal appellate court panel in August ruled 2 to 1 that law enforcement officials can’t request cell phone location records without a warrant.
The government is now asking the full Fourth Circuit Court of Appeals to overrule the panel’s earlier decision, arguing that by choosing to connect to a mobile network, users lose any reasonable expectation that their location is private.
Quoting the dissenting judge, the government wrote that the panel’s decision “flies in the face of the Supreme Court’s well-established third-party doctrine.”
The third-party doctrine is a legal theory that asserts that users voluntarily give up information like location data by subscribing to public services like communications providers, and thus have “no reasonable expectation of privacy” when it comes to that information.
The Fourth Circuit panel had ruled that the third-party doctrine was never intended to allow the government to track people’s entire digital lives over the course of lengthy periods of time, and sided with lawyers for Aaron Graham, a Baltimore man convicted of armed robbery based on details found in seven months of his call records obtained from Sprint without a warrant.
“People cannot be deemed to have volunteered to forfeit expectations of privacy by simply seeking active participation in society through use of their cell phones,” the panel wrote in August.
But the government argued that the Fourth Circuit decision flouted two previous 1970s Supreme Court decisions that had reaffirmed the third-party doctrine.
In United States v. Miller, the court ruled that the contents of original checks and deposit slips were “not confidential communications” and were freely given to a third party — the bank.
In Smith v. Maryland, the court ruled that installation of a pen register, a device that records the numbers of outgoing phone calls, does not constitute a search in violation of the Fourth Amendment because the numbers dialed were shared with the phone company.
What was different about the cell phone case, the Fourth Circuit panel ruled, was that people do not generally know which cell phone tower their phone is connecting to, and do not intentionally offer details about their whereabouts at all times to the cell phone company.
And while subscribers are aware that the provider needs to know which tower to use in order to connect the call, combining seven months of data paints a detailed picture of someone’s everyday life.
Nate Wessler, a staff attorney with the American Civil Liberties Union, said the government “is struggling mightily against the tide.” He explained: “Courts are moving towards recognizing that in the digital age, we need to protect sensitive information. … As of now, in five states, they have to get warrants. … They’re trying to go back to when it was easier. But it will be hard to prevent it from happening.”
The post Government Argues: If Your Mobile Phone Provider Knows Where You Are, Why Shouldn’t We? appeared first on The Intercept.
When Is Assassination Not Assassination? When the Government Says So
It’s one of the most memorable scenes in Apocalypse Now. Martin Sheen’s Green Beret captain is being briefed on his mission to find Col. Walter Kurtz, played by Marlon Brando. “He’s out there operating without any decent restraint, totally beyond the pale of any acceptable human conduct,” a general tells the captain. A civilian spook then gives him a coded order: “Terminate with extreme prejudice.”
The line was no Hollywood creation but a euphemism that came to light in 1969, after a group of real Army Green Berets murdered a suspected Vietnamese double agent. The phrase, some of the soldiers said, was the CIA’s suggestion to them on dealing with the supposed turncoat.
Today, the preferred line for assassination is “targeted killing,” as in Greg Miller’s recent Washington Post exposé revealing that CIA and special operations forces have launched “a secret campaign to hunt terrorism suspects in Syria as part of a targeted killing program.”
How — or if — killing a human with a remote-controlled flying robot differs from, say, a Green Beret killing a rogue colonel, has been discussed and debated for years now. “If it’s premeditated assassination, why call it a ‘targeted killing?’” wrote Margaret Sullivan, the New York Times’ public editor, in 2013, channeling some of the complaints she received from readers.
Scott Shane, a Times national security reporter, had a ready answer: The Obama administration decreed it. He explained that since assassination is banned by executive order, using the term would indicate the administration is deliberately violating the ban. “This administration, like others, just doesn’t think the executive order applies,” he wrote to Sullivan. He crossed off the term “murder” for similar reasons. “This leaves ‘targeted killing,’ which I think is far from a euphemism,” Shane continued. “It denotes exactly what’s happening: American drone operators aim at people on the ground and fire missiles at them. I think it’s a pretty good term for what’s happening, if a bit clinical.”
But is there, beyond the administration’s self-interested rationale, a good reason for the Times and other news outlets (including, on occasion, The Intercept) to dump a perfectly effective word like assassination for a more “clinical” phrase — especially when assassination has such a long history of use by the Times and other news organizations?
“Assassination” was first used in the Times in 1851 and saw its first major spike in 1865 (512 uses), the year President Lincoln was gunned down, before peaking in 1968 (1,087 uses). “Targeted killing” didn’t appear in the newspaper until a 1988 article that touches on violence by Central American regimes against leftist guerillas and their sympathizers. The phrase didn’t break double digits until its 12 uses in 2010, including an article concerning President Obama signing a “secret order authorizing the targeted killing” of U.S.-born cleric Anwar Al-Awlaki, and one titled “Semantic Minefields,” by the public editor at the time, Clark Hoyt, who mentioned the outcry over the phrase (Shane is quoted in that story, too). The phrase would be used 19 times in 2011, a number of the articles focused on the killing of Al-Awlaki; 33 times in 2012; peaking in 2013 with 78 uses; dipping down to 28 in 2014; with 17 so far this year.
About a month after Sullivan’s 2013 article, President Obama gave a speech on counterterrorism policy. “The United States has taken lethal, targeted action against al Qaeda and its associated forces, including with remotely piloted aircraft commonly referred to as drones,” he said. The president likened a suspected terrorist to “a sniper shooting down on an innocent crowd,” but didn’t explain how his use of a drone to shoot down someone never found guilty of any crime in a court of law was different.
I went to the government with the question of how “targeted killing” or “lethal, targeted action” differs from assassination. Ken McGraw, a spokesperson at U.S. Special Operations Command, which oversees one of the two agencies reportedly involved in the new effort in Syria, told me, “I don’t recall ever hearing those terms used in USSOCOM headquarters.” When I took the question to the White House’s National Security Council, spokesperson Peter Boogaard suggested I consult then-State Department Legal Adviser Harold Koh’s March 2010 speech on international law and counterterrorism operations.
In the speech, Koh noted that “some have argued that our targeting practices violate … the long-standing domestic ban on assassinations. But under domestic law, the use of lawful weapons systems — consistent with the applicable laws of war — for precision targeting of specific high-level belligerent leaders when acting in self-defense or during an armed conflict is not unlawful, and hence does not constitute ‘assassination.’”
It was an interesting point given what we now know about the use of so-called signature strikes in which the U.S. government does not know exactly who it is killing, only that the targets appear to be militants. Since these strikes were not “precision targeting of specific high-level belligerent leaders,” I suggested to Boogaard that, by Koh’s reasoning, they might be assassinations and, by similar logic, what Koh also termed “unlawful extrajudicial killing.”
“Will see if there is more we can discuss,” Boogaard replied via email. That was the last I heard from him despite repeated follow-ups.
Micah Zenko, a scholar at the Council on Foreign Relations who studies drone strikes, points out the government will develop legal justifications for any use of force the president decides upon. “I don’t particularly care how you describe it,” he says of targeted killing. “But I certainly understand why people have concerns about how it’s categorized. Words do matter.”
Should we criticize journalists, like those at the New York Times and Washington Post, for adopting euphemisms or watered-down language?
Zenko praised the work of investigative reporters and specifically mentioned Shane and Miller, noting that without them we would know little beyond the administration’s talking points. But with so much of the program shrouded in secrecy and strikes conducted in such distant locations, there are “a lot of points between you and reality,” as Zenko puts it. “When there’s a huge information gap, even really good national security and intelligence journalists become more reliant on sources within government. When you’re more reliant upon those sources, you might be more likely to adhere to — or at least make a case for why they use — the language and justifications that they do.”
The post When Is Assassination Not Assassination? When the Government Says So appeared first on The Intercept.
TSA Doesn’t Care That Its Luggage Locks Have Been Hacked
In a spectacular failure of a “back door” designed to give law enforcement exclusive access to private places, hackers have made the “master keys” for Transportation Security Administration-recognized luggage locks available to anyone with a 3D printer.
The TSA-recognized luggage locks were a much-vaunted solution to a post-9/11 conundrum: how to let people lock their luggage, on the one hand, but let the TSA inspect it without resorting to bolt cutters, on the other.
When the locks were first introduced in 2003, TSA official Ken Lauterstein described them as part of the agency’s efforts to develop “practical solutions that contribute toward our goal of providing world-class security and world-class customer service.”
Now that they’ve been hacked, however, TSA says it doesn’t really care one way or another.
“The reported ability to create keys for TSA-approved suitcase locks from a digital image does not create a threat to aviation security,” wrote TSA spokesperson Mike England in an email to The Intercept.
“These consumer products are ‘peace of mind’ devices, not part of TSA’s aviation security regime,” England wrote.
“Carried and checked bags are subject to the TSA’s electronic screening and manual inspection. In addition, the reported availability of keys to unauthorized persons causes no loss of physical security to bags while they are under TSA control. In fact, the vast majority of bags are not locked when checked in prior to flight.”
In other words: not our problem.
How the Keys Were Hacked
Last month, security enthusiasts and members of a lockpicking forum on Reddit began circulating a nearly year-old Washington Post story about “the secret life of baggage,” and how the TSA handles and inspects airport luggage.
What no one had previously noticed was that the article included close-up photos of the “master keys” to TSA-approved luggage locks — which it turns out, are really easy to copy, as long as you can see the pattern of the teeth and have access to a 3D printer.
The photos were removed from the Post’s website, but not before privacy devotees spread the images far and wide.
Then, according to his self-published timeline, Shahab Shawn Sheikhzadeh, a system administrator and lockpicker, obtained an official-looking document with even more detailed imagery. Sheikhzadeh told The Intercept that anonymous hackers inspired by the Washington Post photos found a 2008 “Guide to Travel Sentry Passkeys” posted on Travel Sentry’s website.
Travel Sentry is the organization responsible for generating and enforcing security guidelines for TSA-approved locks, working with both the government and private manufacturers to guarantee its standards are being met. It does not sell or manufacture locks itself.
Steven Knuchel, a hacker/security researcher who goes by Xylitol or Xyl2k, used the detailed images obtained from the Travel Sentry website to create the kind of files that 3D printers use to produce models.
Since the files were first published, several people have demonstrated that they work, using inexpensive 3D printing plastic called PLA.
The geniuses @TSA require us to use luggage locks for which they have master keys. Now we all have those keys. pic.twitter.com/cdT487Elxj
— J0hnny Xm4s (@J0hnnyXm4s) September 10, 2015
TSA’s Response
TSA’s nonchalant response to the proliferation of master keys is at odds with how the agency has historically advertised the approved locks.
“There’s a difference in how TSA talks about the locks to travelers and the statement they made,” said Chris Soghoian, chief technologist for the American Civil Liberties Union, after hearing the TSA’s statement to The Intercept.
Over the years, TSA has published various blog posts trumpeting the power of the locks to prevent all theft, writing, for instance, that the locks “will prevent anyone from removing items out of your … bags.”
Soghoian described that post as an example of TSA “lying to consumers” in a tweet. “There’s nothing in that blog post about ‘peace of mind’” being the reason for the locks, Soghoian told The Intercept.
Security experts, by comparison, have long recognized that TSA locks do not fully protect your belongings. University of Pennsylvania computer science professor Matt Blaze told Wired that he sometimes picks his own TSA-recognized lock to save time looking for the actual key, because it’s faster.
Chris McGoey, a security consultant specializing in travel safety, told the Intercept that “there are several ways of opening TSA locks short of having a 3D printer.” He explained that “TSA locks on luggage is only one step above having no lock at all especially on soft-sided luggage with zippers.”
The Problem With Backdoors
Although the actual impact remains unclear, the hacking of the master keys is a powerful example of the problem with creating government backdoors to bypass security, physically or digitally.
Most security experts and computer scientists believe backdoors for law enforcement inevitably make systems less secure, and easier for bad actors to break into.
Nicholas Weaver, a computer security researcher at Berkeley, wrote on the Lawfare blog about the TSA locks and how they are “similar in spirit to what [FBI] Director [James] Comey desires for encrypted phones.”
Comey has recently been trying to convince technology companies to design some sort of special way for his agents to access encrypted communications on digital devices. But companies including Apple and Google have resisted this pressure, insisting that developing backdoors will only weaken security that they have worked hard to improve for the sake of average customers around the world.
“In theory, only the Transportation Security Agency or other screeners should be able to open a TSA lock using one of their master keys,” Weaver wrote. “All others, notably baggage handlers and hotel staff, should be unable to surreptitiously open these locks. … Unfortunately for everyone, a TSA agent and the Washington Post revealed the secret. … The TSA backdoor has failed.”
Xylitol, the GitHub user who published the blueprint of the keys, said that was his point. “This is actually the perfect example for why we shouldn’t trust a government with secret backdoor keys (or any kind of other backdoors),” he wrote in an email to The Intercept. “Security with backdoor[s] is not security and inevitably exposes everyone.”
Soghoian tweeted a congratulations to the Post and TSA “for proving the stupidity of key escrow,” the arrangement in which keys needed to decrypt communications are held in escrow to be accessed by a third party if necessary. End-to-end encryption, which the FBI and the Justice Department have continually urged against, only allows for the sender and the recipient of a message to hold onto keys to decrypt the message.
Clarification: An earlier version of this story incorrectly reported that hackers had broken into Travel Sentry’s internal website.
Caption: Master TSA keys for various TSA-approved locks.
The post TSA Doesn’t Care That Its Luggage Locks Have Been Hacked appeared first on The Intercept.
We Got a Letter! I Wonder Who It's From?
Let’s just open this one flap, and then take this letter out, and look a little deeper in. . .
"We're On A Marble, Floating Through Nothing"
These filmmakers struck out to the desert to make an staggering and beautiful to-scale model of the solar system, but what they found might be much deeper.
“This isn’t an article about the evils of free to play manipulation to get you to spend money.

“This isn’t an article about the evils of free to play manipulation to get you to spend money. This is about how we can target you, because we (and our partners) know everything about you.” Some brutal reading at TouchArcade.
This entry passed through the Full-Text RSS service - if this is your content and you're reading it on someone else's site, please read the FAQ at fivefilters.org/content-only/faq.php#publishers.
Counterintelligence Agency Shrugs Off Responsibility for OPM Breach
The nation’s top counterintelligence agency is ducking responsibility for failing to identify or help address the Office of Personnel Management’s poor cyberdefenses before the massive data breach ascribed to the Chinese government, saying that wasn’t its job.
In response to a letter from Sen. Ron Wyden, D-Ore., who asked what the National Counterintelligence and Security Center had done to help OPM secure its systems or root out counterintelligence vulnerabilities, director William Evanina wrote that existing laws governing his office “do not include either identifying information technology (IT) vulnerabilities to agencies or providing recommendations to them on how to secure their IT systems.”
On Wednesday, Wyden blasted the agency for its officious response: “The OPM breach had a huge counterintelligence impact and the only response by the nation’s top counterintelligence officials is to say that it wasn’t their job,” he wrote.
“This is a bureaucratic response to a massive counterintelligence failure and unworthy of individuals who are being trusted to defend America. While the National Counterintelligence and Security Center shouldn’t need to advise agencies on how to improve their IT security, it must identify vulnerabilities so that the relevant agencies can take the necessary steps to secure their data.”
Wyden concluded his letter by repeating his stand against the Cybersecurity Information Sharing Act (CISA), a bill in the Senate that would make it much easier for companies to share personal information on users with the government, with immunity from current surveillance laws. “The way to improve cybersecurity is to ensure that network owners take responsibility for plugging security holes, not encourage the sharing of personal information with agencies that can’t protect it adequately,” wrote Wyden.
The post Counterintelligence Agency Shrugs Off Responsibility for OPM Breach appeared first on The Intercept.
Track: Earthbound - Eight Melodies Orchestral Remix | Album: N/A | Artist: Pascal Michael Stiefel &a
BewarethewumpusNo "Like" button big enough, no "Share" button that can be pressed enough times.
Track: Earthbound - Eight Melodies Orchestral Remix | Album: N/A | Artist: Pascal Michael Stiefel & Rob Platt
Kotaku Soundtrack is a selection of the stuff we’re listening to - and gaming to - at the moment.
This entry passed through the Full-Text RSS service - if this is your content and you're reading it on someone else's site, please read the FAQ at fivefilters.org/content-only/faq.php#publishers.
Library’s Tor relay—which had been pulled after feds noticed—now restored
The New Hampshire library, which last week took down a Tor relay after federal authorities read about it on Ars, has finally restored its important link in the anonymizing network.
The node was turned back on Tuesday evening immediately after the board of the Kilton Public Library in Lebanon voted to do so.
.@LebLibraries Tor relay game strong! @libraryfreedom @torproject #KiltonLibrary pic.twitter.com/YvdGXp2lGB
— Nima Fatemi (@mrphs) September 16, 2015
As Ars reported earlier, the goal of the Library Freedom Project is to set up Tor exit relays in as many of these ubiquitous public institutions as possible. As of now, only about 1,000 exit relays exist worldwide. If this plan is successful, it could vastly increase the scope and speed of the famed anonymizing network. For now, Kilton has a middle relay but has plans to convert it to an exit relay. A middle relay passes traffic to another relay before departing the Tor network on the exit relay.
Judge: It’s Not Nice To Leave Nasty Notes On Speeding Tickets, But It’s Your Constitutional Right To Do So
The Connecticut man was driving in the town of Liberty, N.Y. when he received a speeding ticket for going 82 mph in a 65 mph zone, with a $175 fine attached. He sent back the payment form with a message written on it, “F**k your sh***y town, bitches,” and also crossed out the word “Liberty” and scrawled “Tyranny” in its place.
Local authorities ordered him to show up in court, where he was lectured by a judge, arrested and held for several hours on charges of aggravated harassment, reports the New York Times.
He sued the village, whose officers had arrested him, and last week a federal judge in White Plains ruled that the arrest had violated his First Amendment rights, and allowed his lawsuit to proceed.
“People use language like this all the time,” his lawyer told the Times. “They send letters like this to customer service at Verizon, the I.R.S. When people are unhappy, they vent on forms like that,” he added. “You shouldn’t have to get arrested for it.”
Judge Cathy Seibel ruled that what the man wrote, “though crude and offensive to some, did not convey an imminent threat and was made in the context of complaining about government activity,” and therefore it didn’t violate N.Y.’s aggrvated harassment statute.
“The words here are not inherently likely to provoke violent reaction, they were not directed at anyone in particular, and could not be interpreted as threatening any particular action,” Seibel ruled, according to the Huffington Post.
The case will ultimately be decided by jurors, with Liberty to stand trial for failing to train its police officers regarding the country’s First Amendment, and an assistant district attorney liable for damages, though Seibel dismissed the suit’s claims against the two arresting officers.
U.S. Judge Upholds Right to Scrawl Nasty Note on Speeding Ticket Payment [New York Times]
Scrawling ‘F**k Your S**tty Town Bitches’ On Speeding Ticket Is Free Speech, Judge Finds [Huffington Post]
Arrest of 14-Year-Old Student for Making a Clock: the Fruits of Sustained Fearmongering and Anti-Muslim Animus
There are sprawling industries and self-proclaimed career “terrorism experts” in the U.S. that profit greatly by deliberately exaggerating the threat of Terrorism and keeping Americans in a state of abject fear of “radical Islam.” There are all sorts of polemicists who build their public platforms by demonizing Muslims and scoffing at concerns over “Islamophobia,” with the most toxic ones insisting that such a thing does not even exist, even as the mere presence of mosques is opposed across the country, or even as they are physically attacked.
The U.S. government just formally renewed the “State of Emergency” it declared in the aftermath of 9/11 for the 14th time since that attack occurred, ensuring that the country remains in a state of permanent, endless war, subjected to powers that are still classified as “extraordinary” even though they have become entirely normalized. As a result of all of this, a minority group of close to 3 million people is routinely targeted with bigotry and legal persecution in the Home of the Free, while fear and hysteria reign supreme in the Land of the Brave.
What happened in Irving, Texas, yesterday to a 14-year-old Muslim high school freshman is far from the worst instance, but it is highly illustrative of the rotted fruit of this sustained climate of cultivated fear and demonization. The Dallas Morning News reports that “Ahmed Mohamed — who makes his own radios and repairs his own go-kart — hoped to impress his teachers when he brought a homemade clock to MacArthur High,” but “instead, the school phoned police.”
Despite insisting that he made the clock to impress his engineering teacher, consistent with his long-time interest in “inventing stuff,” Ahmed was arrested by the police and led out of school with his hands cuffed behind him. When he was brought into the room to be questioned by the four police officers who had been dispatched to the school, one of them — who had never previously seen him — said: “Yup. That’s who I thought it was.” As a result, he “felt suddenly conscious of his brown skin and his name — one of the most common in the Muslim religion.”
On Twitter, Anil Dash published a photo, provided by the boy’s family, taken as he was led out in cuffs. Note that he’s wearing a NASA shirt:
There’s absolutely no evidence that this was anything more than a clock, nor any indication of any kind that the talented and inventive freshman built it as anything other than a school project. But even now, “police say they may yet charge him with making a hoax bomb — though they acknowledge he told everyone who would listen that it’s a clock.” According to the BBC, “police spokesman James McLellan said that, throughout the interview, Ahmed had maintained that he built only a clock, but said the boy was unable to give a ‘broader explanation’ as to what it would be used for.”
The Dallas Morning News let Ahmed speak for himself by posting a video of him recounting what happened. Behold the Terrorist Mastermind:
The behavior here is nothing short of demented. And it’s easy to mock, which in turn has the effect of belittling it and casting it as some sort of bizarre aberration. But it’s not that. It’s the opposite of aberrational. It’s the natural, inevitable byproduct of the culture of fear and demonization that has festered and been continuously inflamed for many years. The circumstances that led to this are systemic and cultural, not aberrational.
The mayor of Irving, Beth Van Duyne, became a beloved national hero to America’s anti-Muslim fanatics when, last February, she seized on a fraudulent online chain letter, which claimed that area imams had created a special court based on sharia law. In response, Mayor Van Duyne posted a Facebook rant in which she vowed to “fight with every fiber of my being” the nonexistent “sharia court.” One anti-Muslim website gushed that Irving “is being called ‘ground zero’ in the battle to prevent Islamic law from gaining a foothold, no matter how small, in the U.S. legal system” and hailed her as “the mayor who stood up to the Muslim Brotherhood.”
That led to support for a bill introduced in the Texas State Legislature banning the use of foreign law, which its sponsor made clear was targeted at least in part at these “sharia courts.” The Irving City Council went out of its way to enact a resolution supporting the state bill. It was enacted in June. One of the City Council members who opposed the bill — William “Bill” Mahoney, who “denounced the vote and urged Irving to ’embrace the Muslims'” — then lost his seat in the city election “by a wide margin.” I’ve spoken to Muslim groups in Irving and there is a small but thriving community there, which in turn has produced intense anti-Muslim animus.

People participate in a rally against a proposed mosque and Islamic community center near ground zero in New York, Aug. 22, 2010.
Photo: Seth Wenig/AP
There are all sorts of obvious, extreme harms that come from being a nation at permanent war. Your country ends up killing huge numbers of innocent people all over the world. Vast resources are drained away from individuals and programs of social good into the pockets of weapons manufacturers. Core freedoms are inexorably and inevitably eroded — seized — in its name. The groups being targeted are marginalized and demonized in order to maximize fear levels and tolerance for violence.
But perhaps the worst of all harms is how endless war degrades the culture and populace of the country that perpetrates it. You can’t have a government that has spent decades waging various forms of war against predominantly Muslim countries — bombing seven of them in the last six years alone — and then act surprised when a Muslim 14-year-old triggers vindictive fear and persecution because he makes a clock for school. That’s no more surprising than watching carrots sprout after you plant carrot seeds in fertile ground and then carefully water them. It’s natural and inevitable, not surprising or at all difficult to understand.
The post Arrest of 14-Year-Old Student for Making a Clock: the Fruits of Sustained Fearmongering and Anti-Muslim Animus appeared first on The Intercept.
Saturday Morning Breakfast Cereal - Age of Exploration

Hovertext: I'm just saying, whenever we go to Mars, I'm not going on the first boat.
New comic!
Today's News:













